Lab 02a - Manage Subscriptions and RBAC
Student lab manual
Lab requirements:
This lab requires permissions to create Azure Active Directory (Azure AD) users, create custom Azure Role Based Access Control (RBAC) roles, and assign these roles to Azure AD users. Not all lab hosters may provide this capability. Ask your instructor for the availability of this lab.
Lab scenario
In order to improve management of Azure resources in Contoso, you have been tasked with implementing the following functionality:
-
creating a management group that would include all of Contoso’s Azure subscriptions
-
granting permissions to submit support requests for all subscriptions in the management group to a designated Azure Active Directory user. That user’s permissions should be limited only to:
- creating support request tickets
- viewing resource groups
Objectives
In this lab, you will:
- Task 1: Create custom RBAC roles
- Task 2: Assign RBAC roles
Estimated timing: 30 minutes
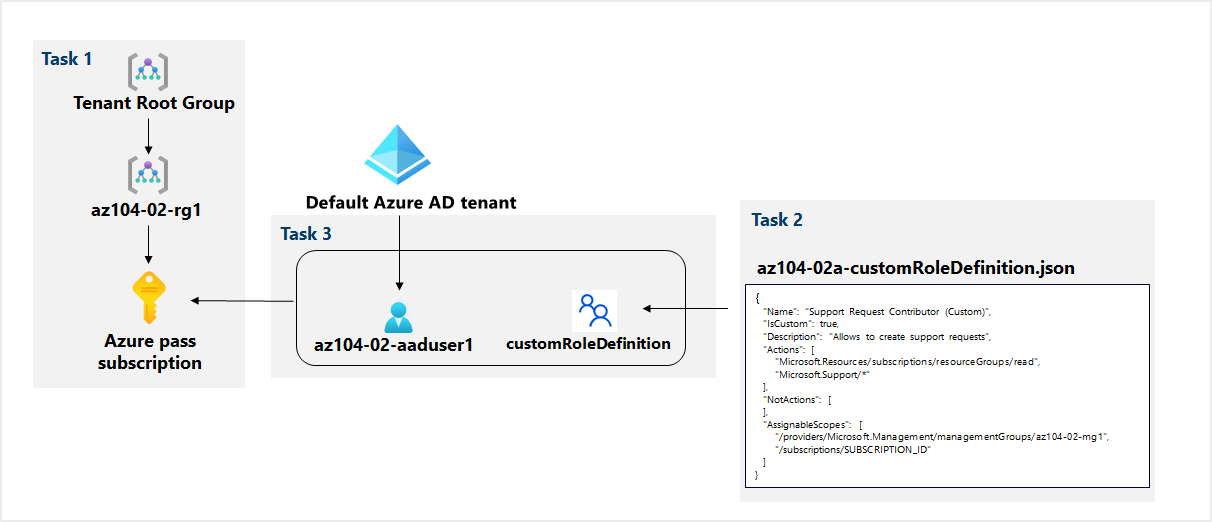
Architecture diagram
Instructions
Exercise 1
Task 1: Create custom RBAC roles
In this task, you will create a definition of a custom RBAC role.
-
From the lab computer, open the file \Allfiles\Labs\02\az104-02a-customRoleDefinition.json in Notepad and review its content:
{ "Name": "Support Request Contributor (Custom)", "IsCustom": true, "Description": "Allows to create support requests", "Actions": [ "Microsoft.Resources/subscriptions/resourceGroups/read", "Microsoft.Support/*" ], "NotActions": [ ], "AssignableScopes": [ "/subscriptions/SUBSCRIPTION_ID" ] }Note: If you are not sure where the files are stored locally in your lab environment, please ask your instructor.
-
Replace the
SUBSCRIPTION_IDplaceholder in the JSON file with the subscription ID you copied into Clipboard and save the change. -
In the Azure portal, open Cloud Shell pane by clicking on the toolbar icon directly to the right of the search textbox.
-
If prompted to select either Bash or PowerShell, select PowerShell.
Note: If this is the first time you are starting Cloud Shell and you are presented with the You have no storage mounted message, select the subscription you are using in this lab, and click Create storage.
-
In the toolbar of the Cloud Shell pane, click the Upload/Download files icon, in the drop-down menu click Upload, and upload the file \Allfiles\Labs\02\az104-02a-customRoleDefinition.json into the Cloud Shell home directory.
-
From the Cloud Shell pane, run the following to create the custom role definition:
New-AzRoleDefinition -InputFile $HOME/az104-02a-customRoleDefinition.json -
Close the Cloud Shell pane.
Task 2: Assign RBAC roles
In this task, you will create an Azure Active Directory user, assign the RBAC role you created in the previous task to that user, and verify that the user can perform the task specified in the RBAC role definition.
-
In the Azure portal, search for and select Azure Active Directory, on the Azure Active Directory blade, click Users, and then click + New user.
-
Create a new user with the following settings (leave others with their defaults):
Setting Value User name az104-02-aaduser1 Name az104-02-aaduser1 Let me create the password enabled Initial password Provide a secure password Note: Copy to clipboard the full User name. You will need it later in this lab.
-
In the Azure portal, navigate back to the subscription and display its details.
-
Click Access control (IAM), click + Add followed by Add role assignment, and assign the Support Request Contributor (Custom) role to the newly created user account.
-
Open an InPrivate/Incognito browser window and sign in to the Azure portal using the newly created user account. When prompted to update the password, change the password for the user.
Note: Rather than typing the user name, you can paste the content of Clipboard.
-
In the InPrivate/Incognito browser window, in the Azure portal, search and select Resource groups to verify that the az104-02-aaduser1 user can see all resource groups.
-
In the InPrivate/Incognito browser window, in the Azure portal, search and select All resources to verify that the az104-02-aaduser1 user cannot see any resources.
-
In the InPrivate/Incognito browser window, in the Azure portal, search and select Help + support and then click + Create a support request.
-
In the InPrivate/Incognito browser window, on the Problem Desription/Summary tab of the Help + support - New support request blade, type Service and subscription limits in the Summary field and select the Service and subscription limits (quotas) issue type. Note that the subscription you are using in this lab is listed in the Subscription drop-down list.
Note: The presence of the subscription you are using in this lab in the Subscription drop-down list indicates that the account you are using has the permissions required to create the subscription-specific support request.
Note: If you do not see the Service and subscription limits (quotas) option, sign out from the Azure portal and sign in back.
-
Do not continue with creating the support request. Instead, sign out as the az104-02-aaduser1 user from the Azure portal and close the InPrivate browser window.
Clean up resources
Note: Remember to remove any newly created Azure resources that you no longer use. Removing unused resources ensures you will not see unexpected charges, although, resources created in this lab do not incur extra cost.
Note: Don’t worry if the lab resources cannot be immediately removed. Sometimes resources have dependencies and take a longer time to delete. It is a common Administrator task to monitor resource usage, so just periodically review your resources in the Portal to see how the cleanup is going.
-
In the Azure portal, search for and select Azure Active Directory, on the Azure Active Directory blade, click Users.
-
On the Users - All users blade, click az104-02-aaduser1.
-
On the az104-02-aaduser1 - Profile blade, copy the value of Object ID attribute.
-
In the Azure portal, start a PowerShell session within the Cloud Shell.
-
From the Cloud Shell pane, run the following to remove the assignment of the custom role definition (replace the
[object_ID]placeholder with the value of the object ID attribute of the az104-02-aaduser1 Azure Active Directory user account you copied earlier in this task):$scope = (Get-AzRoleAssignment -RoleDefinitionName 'Support Request Contributor (Custom)').Scope Remove-AzRoleAssignment -ObjectId '[object_ID]' -RoleDefinitionName 'Support Request Contributor (Custom)' -Scope $scope -
From the Cloud Shell pane, run the following to remove the custom role definition:
Remove-AzRoleDefinition -Name 'Support Request Contributor (Custom)' -Force -
In the Azure portal, navigate back to the Users - All users blade of the Azure Active Directory, and delete the az104-02-aaduser1 user account.
Review Questions
- At what levels can you assign a Role to a user?
- How can you manage multiple subscriptions present in your tenant?
- What are the resource creation limits for a Basic Public IP? How can you check the same?
- What is the difference between a Resource Provider and a Feature scoped to a subscription?
- How can you configure alerts if you cross $100 in your bill for the first 15 days?
Review
In this lab, you have:
- Created custom RBAC roles
- Assigned RBAC roles
- Created Locks